Amazon’s Choice’ best-selling TP-Link router ships with vulnerable firmware
CyberNews researchers found numerous security flaws within the default firmware and the web interface app of the TP-Link AC1200 Archer C50 (v6) router, which may put users at risk of man-in-the-middle and Denial of Service attacks.
With yearly sales of 150 million devices and a 42% share of the global consumer WLAN market, Shenzhen-based TP-Link Technologies Co, Ltd. is the world’s number one manufacturer of consumer-oriented wifi networking products.
Produced by the world’s leading manufacturer and sold by Amazon – the biggest online retailer on the planet – TP-Link routers are so popular that some models are routinely awarded ‘Amazon’s Choice’ badges in the ‘wifi router’ category.
However, few home users realize how many popular consumer-grade router models are plagued by security problems. From default administrator passwords to unpatched vulnerabilities to even pre-installed backdoors, buying the wrong router can have disastrous consequences, such as network infiltration, man-in-the-middle attacks, and router takeovers.
Enter TP-Link AC1200 Archer C50 (v6): this best-selling ‘Amazon’s Choice’ wifi router retails for £34.50 (~$48) in the UK, and is mainly sold within the European market.
Shockingly, it also ships with an outdated version of firmware that is susceptible to numerous known security vulnerabilities.
In addition to being sold with vulnerable firmware, the router comes with another critical flaw: its web interface app suffers from subpar security practices and weak encryption, potentially putting thousands – if not millions – of its owners at risk of cyberattacks.
If you happen to own the TP-Link AC1200 Archer C50 (v6) router, you should install the latest firmware update immediately.
What we discovered
During the course of our security analysis of the TP-Link AC1200 Archer C50 (v6) router, we found multiple unpatched flaws in the default version of the router’s firmware, as well as its web interface app:
- The router is shipped with outdated firmware that is vulnerable to dozens of known security flaws.
- WPS is enabled by default, potentially allowing threat actors to brute-force the router.
- Session tokens are not deleted server-side after logging out of the router app and are accepted for subsequent login procedures.
- The router’s administrator credentials and configuration backup files are encrypted using weak protocols and can be easily decrypted by attackers.
- The default version of the router’s web interface app suffers from multiple bad security practices and vulnerabilities, including clickjacking, charset mismatch, cookie slack, private IP disclosures, weak HTTPS encryption, and more.
On the other hand, most of the known flaws that affected older versions of the router’s firmware, such as code execution during ping procedures and path traversal vulnerabilities, have been patched in the version we analyzed. In addition, HTTP traffic during login and logout procedures on the router’s web interface app is now encrypted using the AES protocol.
However, some of the flaws were only patched halfway through. For example, the backend of the router still seems relatively sloppily secured, which means that someone else can potentially find an entry point within the web interface and re-exploit previously known flaws.
On July 18, CyberNews reached out to TP-Link for comment and to understand whether they were aware of the flaws, and what they plan to do to protect their customers.
After we sent information about the affected TP-Link device, TP-Link stated that the company will force firmware updates on the affected devices, while the owners will receive “relevant notifications” about these updates via their management interface, “whether they manage the device through the web terminal or the mobile app Tether.”
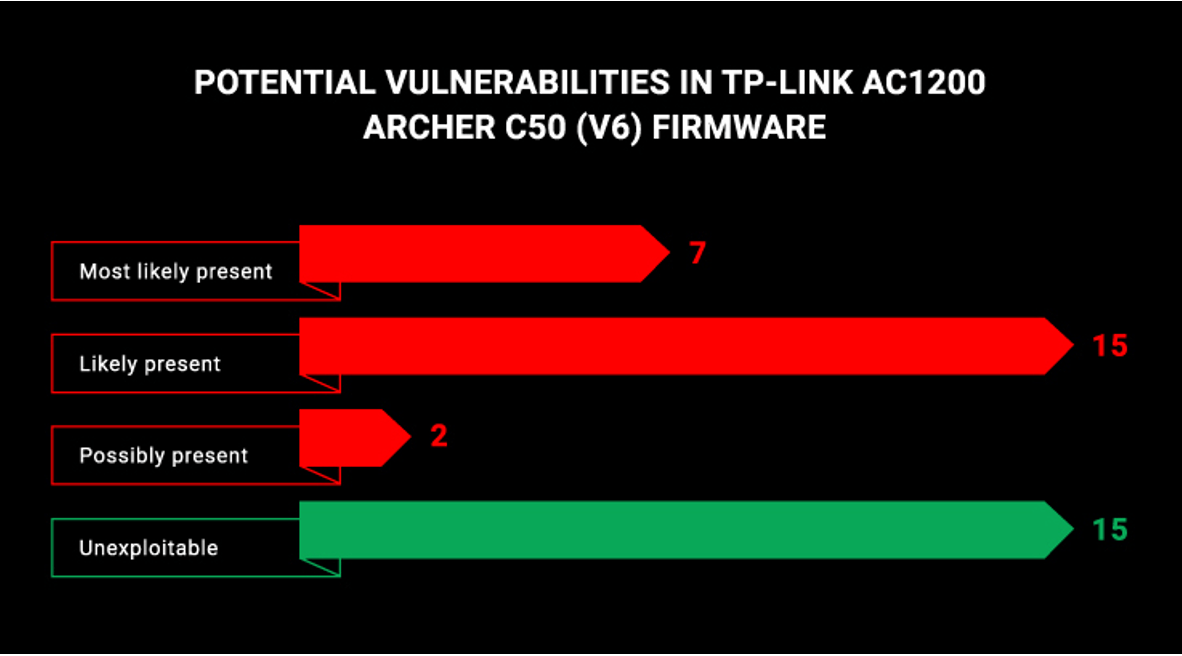
Numerous known vulnerabilities in the default firmware version
Our initial investigation found that the services utilized by the router’s firmware matched 39 publicly-known security flaws listed on the MITRE database of Common Vulnerabilities and Exposures (CVE). We then narrowed down this list by separating the vulnerabilities into 4 categories:
- Most likely present
- Likely present
- Possibly present
- Unexploitable
We identified their likelihood by investigating the router’s kernel and the version numbers of its services, as well as previous detailed reports and open-sourced code that we could look up on GitHub.
Here’s what we found:
As we can see, 24 out of 39 vulnerabilities were identified as potentially present within the router’s firmware, with 15 being ruled out as ‘Unexploitable’.
You may also like
Categories
- Android (3)
- Antivirus (1)
- Artificial Intelligence (AI) (20)
- Automobili (6)
- Bitcoins (6)
- Blockchain (8)
- CAREER (18)
- Cloud Computing (15)
- Cybersecurity (28)
- DEVELOPMENT (20)
- Digital Transformation (62)
- EDUCATION (20)
- FINANCE (99)
- HEALTHCARE (98)
- Home Security Systems (2)
- IGAMING (12)
- Internet of Things (IoT) (28)
- Laptops (8)
- NEWS (351)
- Printers (2)
- PRODUCTS (90)
- RETAIL (31)
- Routers (8)
- SECURITY (60)
- Servers (13)
- SERVICE (12)
- Smartwatches (2)
- Storage (2)
- Streaming Devices (13)
- SUSTAINABILITY (56)
